The Zero Trust approach: Why is protection against internal threats becoming more important?
![]() Gusztáv Krékity
Gusztáv Krékity
![]() 2024.11.21
2024.11.21

The evolving world of cybersecurity requires organizations to defend against both external and internal threats. The Zero Trust approach, gaining popularity, emphasizes that no user or device is automatically trusted, regardless of their position inside or outside the network.

What is Zero Trust?
Zero Trust means all access requests are verified thoroughly before granting access to company resources. It aims to minimize risks by ensuring only authorized individuals can access sensitive information.
Importance of Internal Threat Protection
Internal threats, whether malicious, accidental, or due to compromised devices, can be challenging to detect. Zero Trust addresses this by ensuring constant verification of access requests.
NIS2 Directive Alignment
The European Union’s NIS2 directive, which sets rules for critical infrastructure security, aligns with Zero Trust by promoting continuous monitoring, risk management, and incident response.
Palo Alto Networks Solutions
Prisma Access & Prisma Cloud: Enable secure management of cloud and hybrid environments with continuous verification.
Next-Generation Firewall (NGFW): Provides real-time threat detection, user profiling, and Zero Trust-based access control.
Cortex XSOAR: Combines automation and intelligent incident management for rapid response to threats.
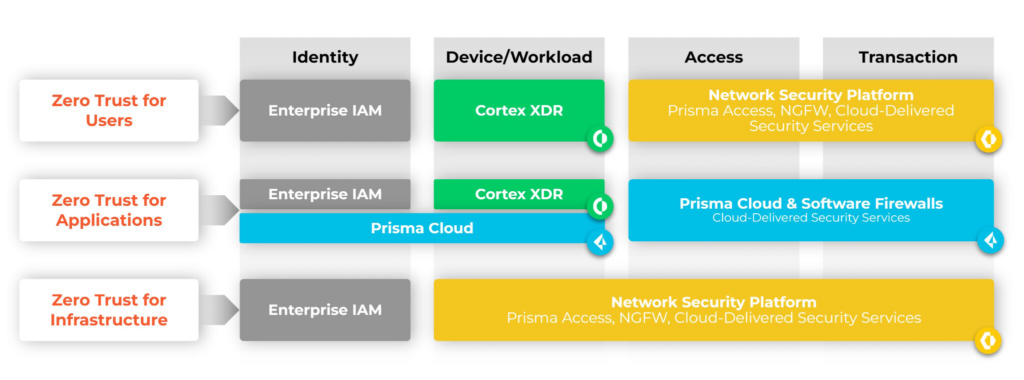
How to Get Started with Zero Trust
- Identify Critical Resources: Ensure only authorized users have access.
- Implement Strong Access Controls: Use MFA and strict access rules.
- Monitor Continuously: Utilize tools like NGFW and Prisma for real-time monitoring.
- Automate Incident Response: Leverage tools like Cortex XSOAR for efficient threat management.
Zero Trust is more than a trend; it is crucial for effective cybersecurity in today’s digital landscape. Palo Alto Networks solutions help organizations secure both internal and external threats, protecting valuable data and resources.
Read the full article on our International subsidiary’s website by clicking on the image.


