Endpoint Protection Solutions for NIS2 Compliance
![]() Gusztáv Krékity
Gusztáv Krékity
![]() 2024.09.02
2024.09.02

In today’s digital age, advanced endpoint protection is crucial for defending against cyber threats. Systems like Endpoint Protection Platform (EPP), Endpoint Detection and Response (EDR), and Extended Detection and Response (XDR) help protect devices and systems from attacks. The EU’s new NIS2 Directive imposes additional requirements for cybersecurity, emphasizing the need for these advanced solutions.
NIS2 Directive and Endpoint Protection
The NIS2 Directive aims to unify and strengthen cybersecurity standards across the EU, especially for critical infrastructure. It mandates preventive measures, incident management, and continuous risk analysis.
- Preventive Measures: NIS2 requires organizations to implement solutions like EPP, EDR, and XDR to prevent endpoint attacks.
- Incident Management: Systems like EDR and XDR help organizations detect and quickly respond to threats.
- Continuous Risk Management: XDR provides comprehensive risk management through integrated threat detection.
EPP, EDR, and XDR Overview
Endpoint Protection Platform (EPP)
EPP solutions are designed to provide foundational security against common cyber threats such as malware, viruses, and phishing. They work by preventing known threats before they reach the endpoint, offering basic capabilities such as virus scanning, endpoint firewall protection, and anti-ransomware features. EPP is easy to implement and suitable for organizations that need essential security tools without the complexity of more advanced solutions.

Endpoint Detection and Response (EDR)
EDR tools focus on continuous monitoring of endpoint activities, allowing for the detection of suspicious behavior and swift incident response. Unlike EPP, which focuses on prevention, EDR aims to detect advanced threats that have bypassed initial defenses. It provides security teams with detailed insights, helping them understand and mitigate the impact of ongoing attacks. Ideal for medium to large organizations where proactive threat hunting and rapid response capabilities are critical.
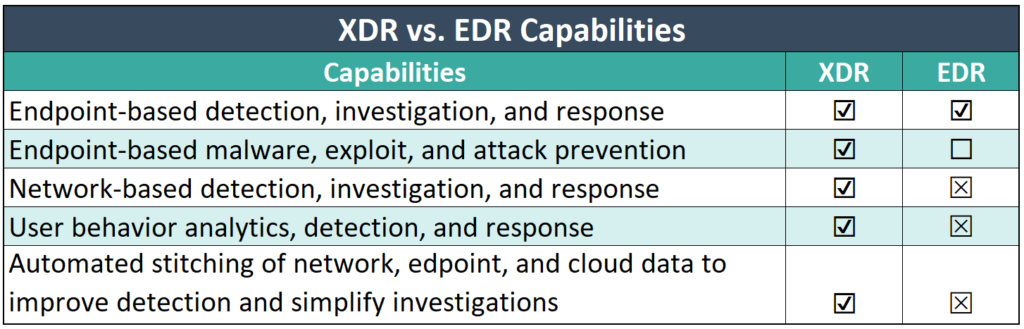
Extended Detection and Response (XDR)
XDR takes a broader approach to cybersecurity, combining insights from multiple layers of an IT environment, including endpoints, networks, and cloud systems. XDR goes beyond EDR by aggregating data from various sources, providing a more unified and comprehensive view of an organization’s security posture. The system automates threat detection and response, reducing response time and providing an overarching defense strategy. Good choice for large enterprises and organizations with critical infrastructure that need a comprehensive and automated security solution to ensure compliance with standards like NIS2.
Processes and Expertise for NIS2 Compliance
Beyond technology, effective processes and skilled personnel are key. Regular risk analysis, incident management protocols, and software patching are essential. Additionally, continuous training and awareness help ensure staff understand and mitigate cybersecurity risks.
Processes:
- Risk Analysis and Audits: Regular risk assessments and security audits help identify and address vulnerabilities.
- Incident Management: Clear protocols for detecting, reporting, and mitigating incidents ensure a quick response.
- Software Updates: Structured processes for applying software updates and patches to close vulnerabilities.
Competencies:
Training Programs: Ongoing training to help staff recognize threats and understand their cybersecurity roles.
Summary
Advanced endpoint protection solutions, combined with appropriate processes and expertise, are vital for meeting the NIS2 Directive’s requirements and tackling modern cyber threats. By carefully assessing their needs and aligning technology choices with organizational goals, companies can create a robust cybersecurity posture that keeps them compliant and well-protected.
Read the full article on our International subsidiary’s website by clicking on the image.


