Vulnerability Management: The Cornerstone of IT Security?!
![]() Gusztáv Krékity
Gusztáv Krékity
![]() 2024.09.26
2024.09.26
IT security is a crucial aspect of business operations in today’s digital age. With the rise of digitization and complex systems, effective IT security requires not only technology but also well-planned processes—and vulnerability management is a key component.
What is Vulnerability Management?
Vulnerability management is the ongoing process of identifying, prioritizing, and mitigating vulnerabilities in systems and networks. It is proactive, continuously adapting to changes and addressing new risks quickly.
Why is Vulnerability Management Important?
- Proactive Protection: It identifies and fixes vulnerabilities before they become serious threats.
- Cost Efficiency: Preventing incidents is much cheaper than recovering from attacks.
- Regulatory Compliance: Regular vulnerability assessments help meet standards like GDPR and PCI-DSS.
- Business Continuity: Effective vulnerability management reduces the risk of system downtime and data loss.
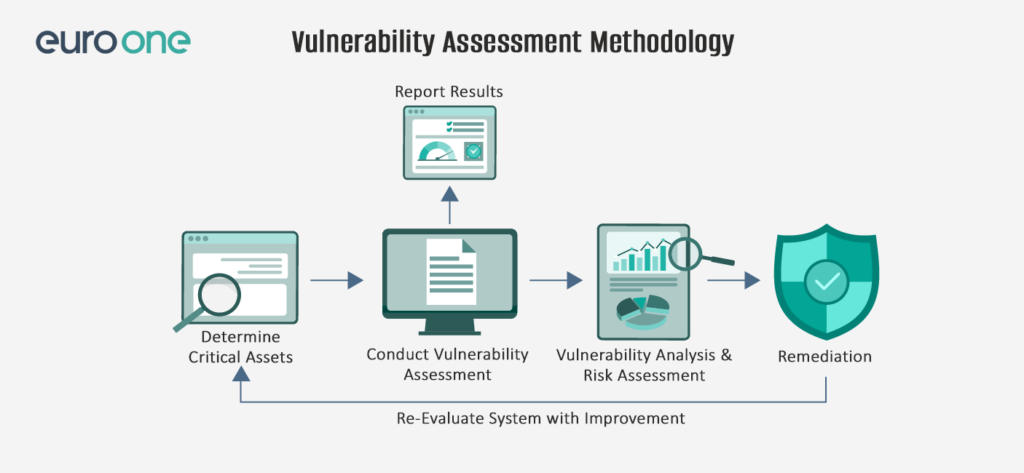
Beyond Tools: The Role of Processes and Expertise
Using the right IT security tools is important, but effective vulnerability management also relies on well-designed processes and human expertise. Key factors include:
- Process Development: Establishing flexible processes that adapt to new threats and technologies.
- Change Management and Testing: Regular updates and testing ensure that vulnerabilities are addressed before they can be exploited.
- Human Expertise: Skilled personnel are essential for interpreting risks and making informed decisions.
- Continuous Improvement: Vulnerability management is an evolving field that requires continuous process review, training, and innovation to keep pace with new threats.
In summary, vulnerability management plays a vital role in securing IT systems by combining technology, well-developed processes, and human expertise. This coordination ensures the security and smooth functioning of business operations.
Read the full article on our International subsidiary’s website by clicking on the image.


