New AI Analyst in our SOC: 3-Month Review
![]() Gábor Szabó
Gábor Szabó
![]() 2025.07.01
2025.07.01

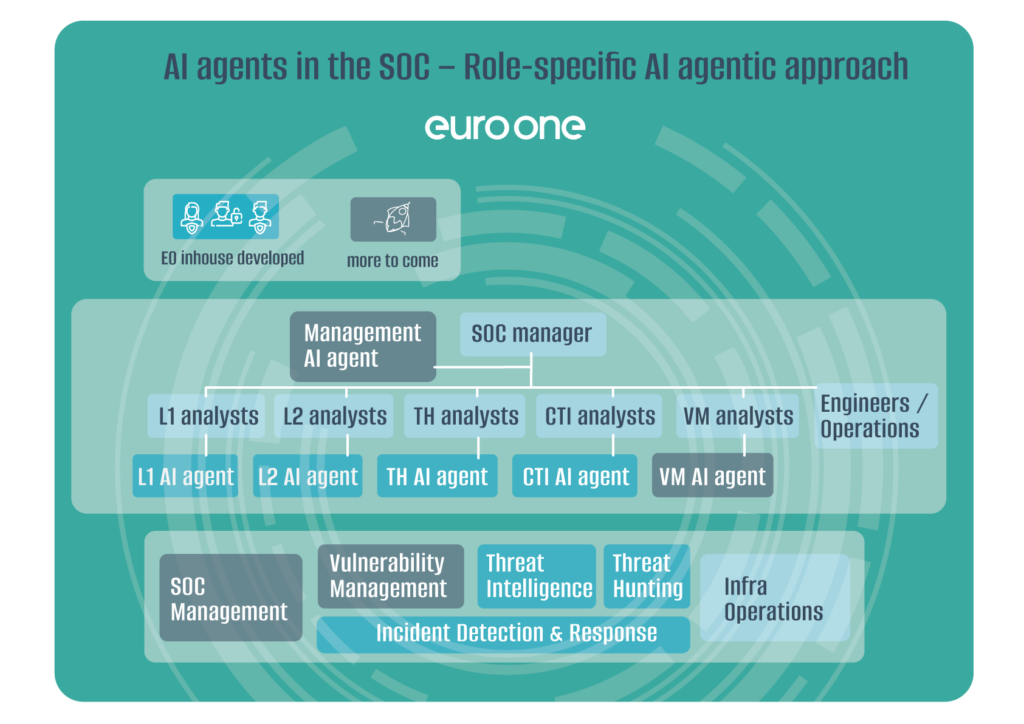
Why we needed AI in our SOC?
Managing growing volumes of data and incidents is a major challenge for Security Operations Centers (SOCs). Analysts often face burnout due to repetitive administrative tasks. To address this, an AI analyst was introduced to improve incident management efficiency.
Why Netwitness AI?
Unlike generic models, Netwitness’ AI module is tailored for SOC environments. It allows:
- Custom prompt logic trained on internal context
- Integration with systems like Active Directory
- Role-specific support (L1/L2 analysts, threat hunters, managers)
- Continuous developer feedback
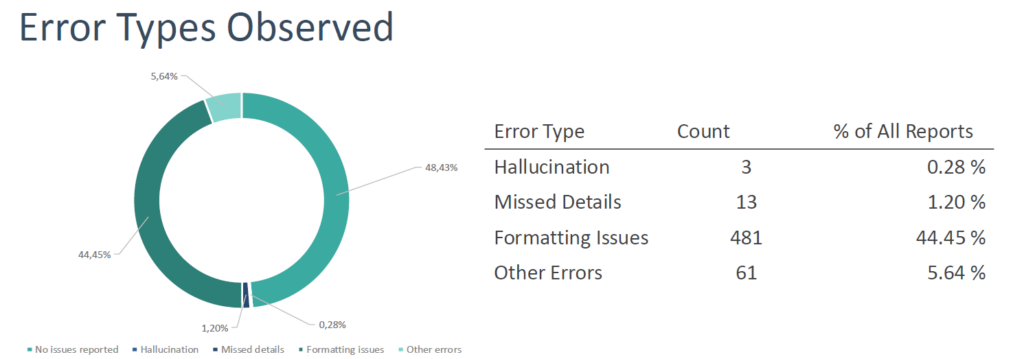
Results After Three Months
- 1,082 incidents analyzed
- Our colleagues validated the data of AI.
- 0.28% hallucination rate
- Most errors (86%) were minor formatting issues
- Negligible content errors
Time & Cost Savings
Average analysis time: 4.5 minutes
Cost per incident: $0.33
Biggest savings were seen in correlation engine and UEBA alerts.
Team Experience
Initially skeptical, SOC staff now value the AI for:
- Time savings
- Automatic context detection (e.g., real user IDs)
- Supporting junior analyst training
Conclusion
The AI analyst enhances—not replaces—human work. It speeds up processes, reduces admin burden, aids training, and continuously improves. In SOCs, AI is no longer future tech—it’s a practical tool today.
Read the full article on our International subsidiary’s website by clicking on the image.


