Protection against email attacks: solutions from Trend Micro
![]() Gusztáv Krékity
Gusztáv Krékity
![]() 2024.10.24
2024.10.24

Business Email Compromise (BEC) is a significant cyber threat where attackers send deceptive emails appearing to come from trusted sources, manipulating victims into transferring money or divulging information. BEC often lacks links or attachments, making detection challenging for traditional security systems.

Key Challenges of BEC Attacks
- Personalization and Deception: Attackers craft highly personalized emails by researching the target’s organization and executives, making these fraudulent emails appear legitimate and hard to identify.
- Spoofing and Social Engineering: Attackers use spoofing to fake email addresses and social engineering to exploit human trust, bypassing traditional security systems.
- Limitations of Traditional Security: Traditional filters and virus scanners often fail to detect BEC attacks since they lack malicious content, allowing these threats to evade detection.
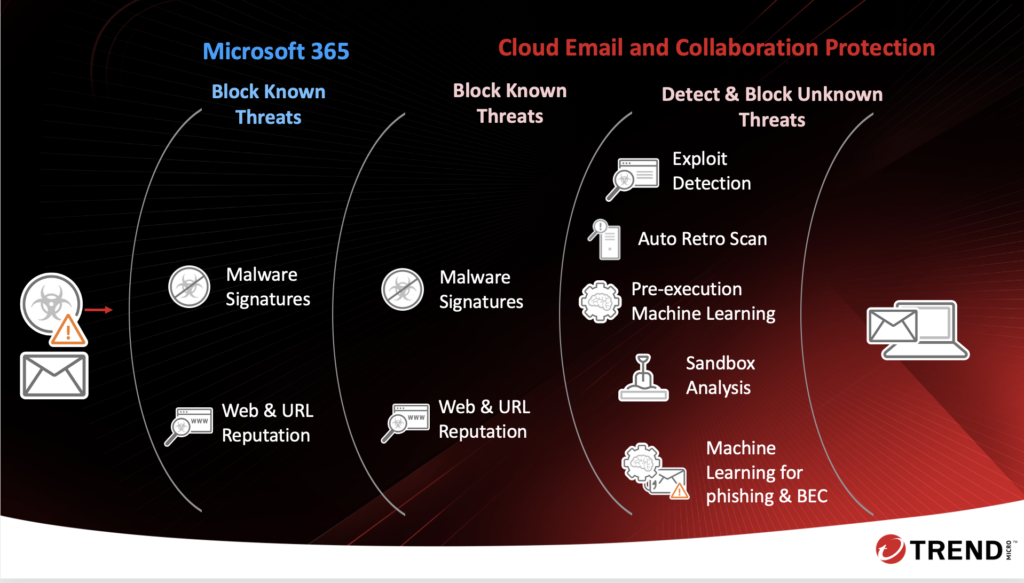
Trend Micro’s Advanced Solutions
- Writing Style DNA: Analyzes writing style to detect deviations, helping identify impersonation attempts.
- AI-based Security Systems: Uses AI to analyze content and metadata, adapting to emerging threats.
- Sandboxing and Emulation: Tests emails in a secure environment to detect anomalies before reaching users.
- Integrated Email Security Solution: Combines Writing Style DNA, AI analysis, and sandboxing to offer comprehensive protection against BEC, reducing risks effectively.
Conclusion
BEC attacks are sophisticated and evolving threats. Trend Micro’s solutions—Writing Style DNA, AI-based analysis, sandboxing, and the integrated Email Security Solution—offer robust protection, helping organizations stay ahead of cybercriminals.
Read the full article on our International subsidiary’s website by clicking on the image.


