Next Gen SOC – The Core of Modern Cyber Defense
![]() Ivett Dobay
Ivett Dobay
![]() 2025.11.13
2025.11.13

In today’s digital landscape, cybersecurity is not just an IT responsibility—it’s the foundation of trust in every organization. The Security Operations Center (SOC) is the heart of defense, monitoring, analyzing, and managing threats 24/7 to keep business operations secure and uninterrupted.
How SOC Works
The SOC operates as a continuous security cycle, integrating people, processes, and technology to detect and stop threats before they cause harm.
1. Monitoring and Data Collection
Networks, servers, and applications are constantly monitored. Data from firewalls, antivirus tools, endpoint protection, and SIEM platforms is centralized for analysis.
2. Analysis and Detection
SOC analysts interpret the data, identify unusual activity, and decide which alerts need immediate action—for instance, a suspicious login from two distant locations.
3. Incident Response
When a real threat emerges, quick and coordinated action isolates the attack, limits damage, restores systems, and ensures business continuity.
4. Continuous Improvement
Every incident becomes a learning opportunity. Lessons learned help refine defense rules, automate tasks, and strengthen proactive threat hunting.
Why Errors Are Costly
Small misses can snowball into major impact:
- Data leakage: undetected infected endpoints can expose confidential information.
- Service downtime: compromised critical systems disrupt operations.
- Reputation hit: public incidents erode customer trust.
- Financial loss: recovery, outages, and legal exposure add up fast.
NIS2 and SOC Maturity
The EU’s NIS2 Directive raises the bar for cybersecurity. Compliance now requires not only technology but also process maturity.
A well-functioning SOC ensures:
- Maintaining visibility through continuous monitoring,
- Detecting anomalies quickly and accurately,
- Ensuring documented, reportable responses,
- Providing transparent incident management and traceability.
A mature SOC not only meets regulatory standards but also strengthens business resilience and trust.
EURO ONE and SOCWISE: Trusted Security Partners
EURO ONE and its subsidiary SOCWISE combine over two decades of experience in protecting enterprises and critical infrastructure. Working with global partners, they deliver automated SOC processes and international-level expertise—constantly staying ahead of evolving threats.
Our Security Competence Center:
- Has over 20 years of experience safeguarding corporate and critical infrastructures,
- Provides automated SOC processes and global-standard services,
- Continuously innovates to stay ahead of evolving threats.
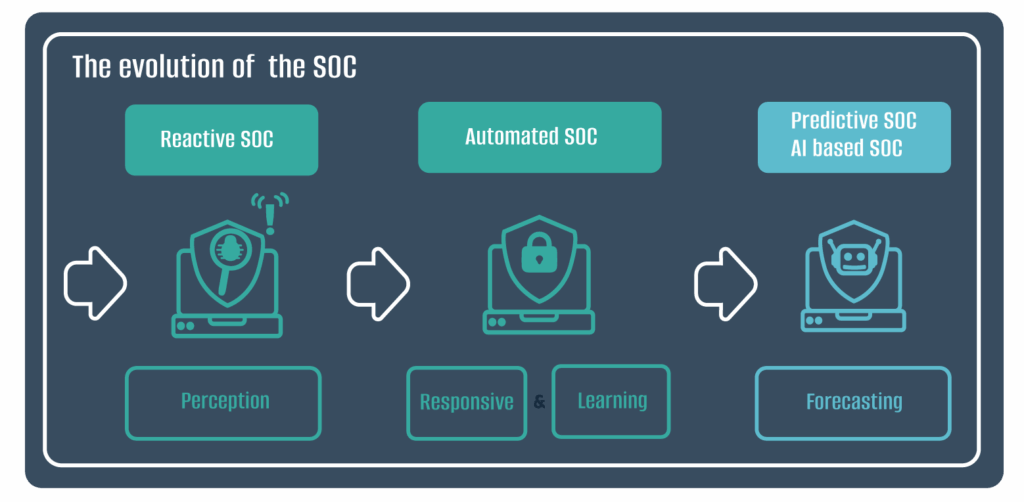
The Future of SOC
As cyber threats accelerate, human capacity alone is no longer enough. The next-generation SOC combines human expertise with intelligent automation and machine learning—ensuring organizations can keep pace with a fast-changing threat landscape.
Read the full article on our International subsidiary’s website by clicking on the logo:


