Data leaks and ransomware in 2025 – what can we learn from Verizon’s annual report?
![]() Ivett Dobay
Ivett Dobay
![]() 2025.05.22
2025.05.22
Verizon’s 2025 DBIR, based on 12,000+ real incidents, offers key insights into today’s cyber risks. These findings are highly relevant for Hungarian organizations facing growing digital exposure.
Evolving Tactics, Familiar Goals – Behind the statistics
While attack methods change, the goal stays the same: infiltrate, extract data, and profit.
Top Threats to Watch
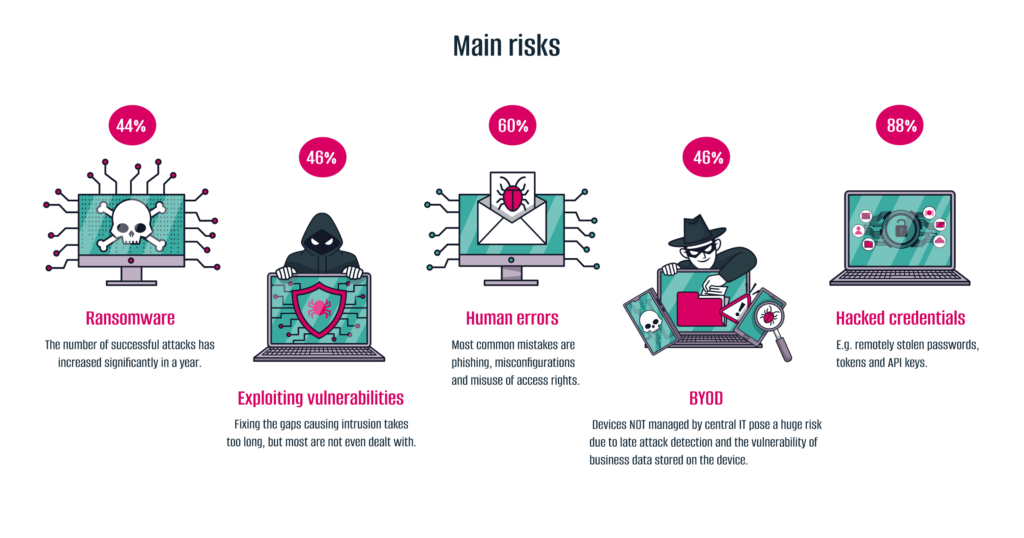
- Ransomware appears in 44% of breaches — a 37% rise year-over-year.
- Human error plays a role in 60% of cases — from phishing to misused privileges.
- Credential theft drives 88% of web app attacks — stolen passwords and tokens are key entry points.
- Patch delays: Fixes take a median of 32 days — too slow to block threats.
- Personal devices: In 46% of breaches, stolen credentials came from unmanaged BYOD devices.
Why is this important in Hungary?
While the report is global, its lessons are also valid for Hungary. In Hungary as well, more and more organizations are using SaaS services, remote access, hybrid working – all of which increase the attack surface.
- The proportion of incidents caused by third parties doubled (from 15% to 30%).
- Vulnerabilities in border protection assets have become almost 8 times more frequent targets, while the median time to update is 32 days.
Building Better Defenses
CIS Controls provide a roadmap:
Tech measures:
- Enforce Zero Trust
- Apply MFA on all external systems
- Strengthen patching and endpoint security
- Enable logging and monitoring
People and process:
- Track assets and permissions
- Deliver security training and phishing drills
- Set up fast incident response protocols
AI: A New Risk Vector?
- Attackers use generative AI for:
- Realistic phishing emails
- Localized malware using AI-generated code
- 15% of employees use AI at work — often unsafely or unregulated.
Risks:
- Uploading company documents to AI systems may lead to data leakage through untrusted platforms.
- Employees often don’t realize these tools aren’t safe for corporate use — especially risky when used on unmanaged BYOD devices.
AI in Defense – Promise and Pitfalls
GenAI helps defenders, too:
- Detects phishing through language patterns
- Automates SOC workflows
- But it also brings new risks: prompt injection, false outputs, and misuse.
The Coming AI Regulation Challenge
- The report signals that AI regulation in business will soon become essential.
- Enforce data minimization and limit access with least privilege
Pre-enabled AI on mobile devices adds hidden risks and promotes shadow IT.
Summary
Cybersecurity today is a people, tech, and strategy issue. As threats grow — ransomware, AI-driven attacks, BYOD exposure — we must stay ahead. At our InfoSec division, we combine advanced tools, training, and governance to help clients secure their systems and use AI responsibly.
Read the full article on our International subsidiary’s website by clicking on the image.


