Application of Cyber Security TTP Principles in IT Security
![]() Gusztáv Krékity
Gusztáv Krékity
![]() 2025.01.30
2025.01.30
The world of cybersecurity constantly evolves, and organizations must stay vigilant against emerging threats. A key tool for understanding attackers and developing defenses is the TTP (Tactics, Techniques, and Procedures) framework. Here, we outline the basic principles of TTP and their practical application in IT security.
What is TTP?
- Tactics: The overall goals or strategies of attackers, such as obtaining data or disrupting systems.
- Techniques: The methods or tools used to achieve these goals, like exploiting vulnerabilities or employing social engineering.
- Procedures: The specific steps attackers take, detailing how techniques are carried out.
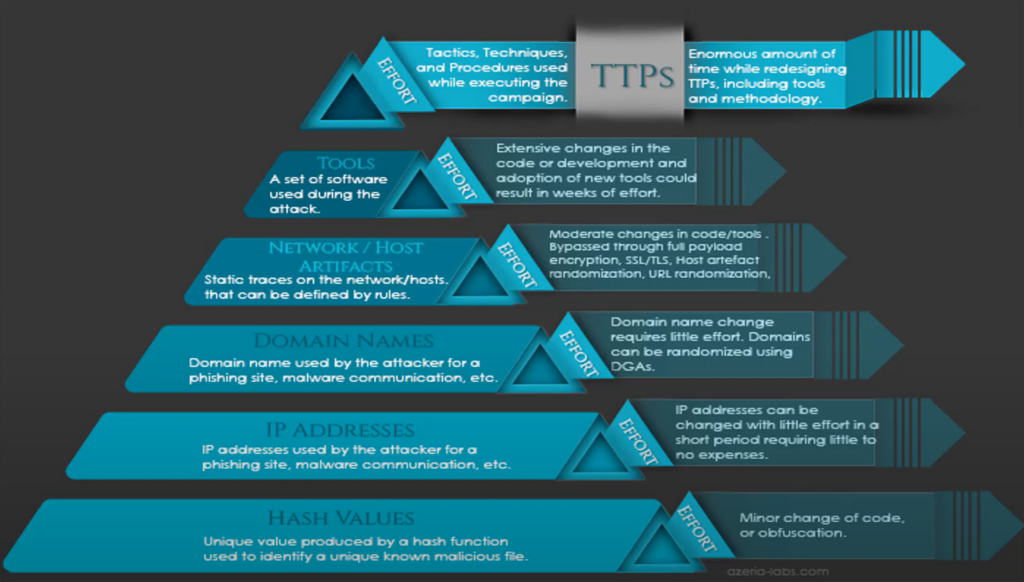
Why is TTP Important in IT Security?
- Tactics: Understanding attacker goals helps IT professionals identify targets and develop strategies to protect them.
- Techniques: Recognizing attack methods allows for specific defenses, such as enhanced training against social engineering or consistent patch management.
- Procedures: Analyzing attack steps helps security teams detect suspicious activities and prepare tailored defenses.
Integrating TTP-Based Protection
By incorporating TTP into IT security strategies, organizations can proactively defend against threats. This approach enhances threat detection, improves incident response, and strengthens overall cybersecurity.
Conclusion
Understanding TTP principles is crucial for anticipating and preventing cyber attacks. As attackers continually evolve, a TTP-based approach allows organizations to stay ahead, improving their overall security posture.
Read the full article on our International subsidiary’s website by clicking on the image.


